Related Posts

Why You Should Start Your Year With a Technology Assessment
Wealth management firms are grappling with an increasing demand for transparency, personalization,... read more

Ransomware Group BlackCat/ALPHV Weaponizes SEC Disclosure Rules
The digital era has brought with it an increase in cyber threats... read more

Cybersecurity Guidance for Financial Advisors: Protecting Your Clients and Their Assets
In today's digital age, financial advisors have more responsibilities than ever before.... read more

What Is Business Process Management, and Why Wealth Management Firms Must Embrace It Now
What is Business Process Management (BPM)? Find out why wealth management firms... read more
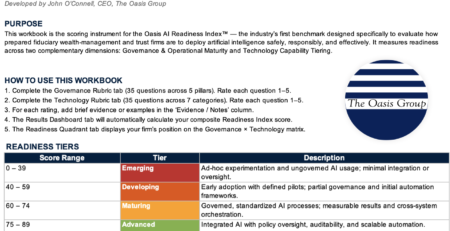
The Oasis Group’s AI Readiness Index: First Maturity Benchmark for Wealth Management Industry
The Oasis AI Readiness Index™ is the industry’s first maturity benchmark... read more

The Limitations of SOC2 Audits in Preventing Cybersecurity Breaches: A Critical Analysis
SOC2 audits have become the de facto standard for demonstrating security compliance... read more

Where Does AI Fit in Your Firm’s Future?
This article provides a brief guide to the AI technologies available today,... read more

Navigating the Digital Minefield: A Guide for Financial Advisors on TikTok and Temu
In an era where digital convenience intersects with unparalleled risks, financial advisors... read more

The AI Revolution Is Here: Why Most Wealth Management Firms Are Getting Left Behind
What's happening with AI in wealth management isn't just another tech upgrade;... read more

Secure Your Digital Life by Using Multiple Email Accounts
In today's fast-paced digital world, where cyber threats are always lurking, safeguarding... read more

