Related Posts

Natural Language Research: Google Finance’s Deep Search Changes Investment Workflows
Traditional research workflow involves multiple database queries, manual data aggregation, and spreadsheet... read more

Responding to Digital Identity Theft: A Guide for Financial Advisors
When you discover your identity has been used in a pump and... read more

The Strategic Imperative of Appointing a Chief Growth Officer
In the dynamic landscape of wealth management, the quest for sustainable growth... read more

Your Wealth Management CRM Doesn’t Have Sales Stages – And It’s Costing You Clients
Your conversion process has stages whether your CRM acknowledges them or not.... read more

Why Your Wealth Management CRM Can’t Talk to Your Email Marketing Platform (And Why That’s Hurting Your Growth)
CRMs and email marketing platforms exist in parallel universes that don't communicate... read more

Regulated Prediction Markets: The New Asset Class Wealth Managers Can’t Ignore
For most of the past two decades, prediction markets were treated as... read more

Using Claude to Create a Monte Carlo Retirement Simulation
Monte Carlo simulations have become an invaluable tool for financial advisors and... read more

Achieving Focus Through Diagnostic Interviewing
Financial advisors have one of the most important jobs out there -... read more
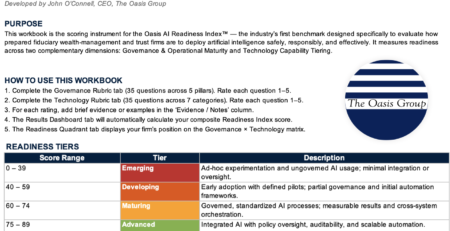
The Oasis Group’s AI Readiness Index: First Maturity Benchmark for Wealth Management Industry
The Oasis AI Readiness Index™ is the industry’s first maturity benchmark... read more

The CTO’s Impossible Choice: Govern Shadow AI or Watch Your Firm’s Data Walk Out the Door
While your compliance team debates whether to allow the latest LLMs, most... read more

